Archive for March, 2009
Learn to Detect Spyware etc
Posted in Uncategorized on March 24, 2009| Leave a Comment »
Swap it Encrypt Service
Posted in Uncategorized on March 24, 2009| Leave a Comment »
Swapt! Encrypt it! – The Internet’s Newest and Best File Transfer Company Published on Tuesday, March 24, 2009
The recently launched Swap it! Encrypt it! file transfer service offers users an inexpensive, no membership way to send large files, and Swap it! Encrypt it! Lite is a great way to send small files (up to 25MB) for free! March 23, 2009 – Swap it! Encrypt it!, the internet’s newest file transfer company, delivers users an unparalleled file transfer service at prices so low it seems too good to be true. Unlike ‘You Send It’ and other major file transfer companies, Swap it! Encrypt it! offers users the ability to transfer files between home computers or mobile devices from one simple web page (no mobile application required). Swap it! Encrypt it! was designed to provide users with a fast (easy to use) inexpensive way to transfer files quickly and safely. Advantages – Transfer files for as low as .99 cents – Free confirmation e-mails – Works for mobile devices – No membership or sign up required – Lowest prices on-line Send small files for free with Swap it! Encrypt it! Lite and see for yourself how excellent Swap it! Encrypt it!’s file transfer service is. Swap it! Encrypt it! Lite does not require a membership or sign up! Advantages – Send files up to 25 MB in size for free – No membership or sign up required About Swap it! Encrypt it! Swap it! Encrypt it! was launched in February 2009 by Taylor Steele and Graham Laverty. http://www.swapitencryptit.com is recognized by its clients as the least expensive and best way to transfer files between home computers or mobile devices over the internet. Taylor Steele Owner/Operator Vancouver, Canada 1-604-566-0922 http://www.swapitencryptit.com
zSHARE – hackRppl2_clip0.wmv
Posted in Uncategorized on March 22, 2009| Leave a Comment »
Documentary on Hacking CommunityMisunderstood group
Vodpod videos no longer available.
Identity Theft
Posted in Uncategorized on March 16, 2009| Leave a Comment »
Phishing and Employee Awareness
Posted in Uncategorized on March 16, 2009| Leave a Comment »
One of the frequently proposed ideas for reducing bank fraud is to train customers to identify and ignore phishing emails.
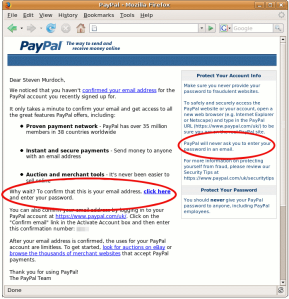
The problem with this approach is that the criminals sending such emails quickly adapt to circumvent the advice given to customers, as can be seen in this quiz. Even worse is that the emails sent by banks often resemble phishing attempts, and sometimes directly violate the advice given to customers. With this “do as I say, not as I do” approach, it is no surprise that customers regularly fall for the scams. In fact, sometimes a legitimate email look so fake that the bank’s own security staff think it’s a phish. And it’s not just banks which are slipping up. I received an email from Paypal, asking users to “click here and enter your password” despite the warning on the same page: “PayPal will never ask you to enter your password in an email”. What can customers be reasonably expected to do, given this type of training? I simply closed my account. Email is a valuable sales channel for banks, and marketing teams evidently have not being willing to sacrifice it, despite the (justified) concerns of the security departments. This fact, coupled with the weak authentication schemes currently deployed, makes life for fraudsters easy. Paypal have tried one alternative approach – a two-factor token – but these are still vulnerable to attack. Strong security solutions, accepted both by customers and marketing, are needed to mitigate the large damages from fraud we see today.
PBS Series CYBER WARS
Posted in Uncategorized on March 16, 2009| Leave a Comment »

A entire 52 minute program here in six consecutive chapters.
– Series Online from Frontline by PBS
http://www.pbs.org/wgbh/pages/frontline/shows/cyberwar/view/1_hi.html
This looks at how Denial of Service, Malware, Virus etc is a national invasion and a threat to national security
Introduction to Information Security
Posted in Uncategorized on March 12, 2009| Leave a Comment »
Vodpod videos no longer available.
12 Steps to IT Security
Posted in Uncategorized on March 12, 2009| Leave a Comment »
Twelve Steps to Protecting your Business or Organization
1. Passwords
Use strong passwords, routinely change them, longer passwords with a combination of numbers and letters, try replacing your passwords with vowels with numbers
2 Email
Look for Virus in Emails and automatic downloads
3.Anti Virus Software
Install and Maintain anti-virus applications
4. Firewalls
Use a Firewall
5.Software and User Accounts
Un-install un-used software and user accounts
6. Access
Establish physical access controls for all computer equipment, secure log-in for computers
7.Backup
Create backups of important files and software
8 Software Updates
Routine updates of all software, patches and security alerts
9 Network
Implement network security, control access to network
10 Data Security
Limit access to sensitive data and confidential data, encrypt data including on memory sticks etc and through email
11 Risk
Perform a routine security risk assessment and checklist and follow within your management plan, have practical policies and procedures
12. Technical Help
Obtain outside technology help if needed
Google Talk on E Crime
Posted in Uncategorized on March 12, 2009|
oogle TechTalks
January 24, 2006
Phillip Hallam-Baker
Dr Hallam-Baker is a leading designer or Internet security protocols and has made substantial contributions to the HTTP Digest Authentication mechanism, XKMS, SAML and WS-Security. He is currently working on the DKIM email signing protocol, federated identity systems and completing his first book, The dotCrime Manifesto which sets out a comprehensive strategy for defeating Internet crime.
Dr Hallam-Baker has a degree in Electronic Engineering from Southampton University and a doctorate in Computer Science from the Nuclear Physics Laboratory at Oxford University.
Google Tech Talk on Cybercrime
Posted in Uncategorized on March 12, 2009| Leave a Comment »
http://www.veoh.com/browse/videos/category/technology/watch/v16067993dqGfE5sr
Columbia Alumni Event 2008: Protecting the World from Cybercrime
Google Tech TalksAugust 28, 2008ABSTRACTSince 2005, over 230 million customer records have been lost or stolen in




